The introduction of digital money has made transactions effective and efficient. However, this also proposes new problems and security risks. Double spending is an issue in blockchain that refers to a digital currency being spent more than once. This issue is extremely rare but remains possible, so it needs to be addressed. If double spending is left unchecked, it will undermine the integrity of digital currencies.
This article will explain the double spending problem, along with some of the associated attacks.
What is double spending?
The effect of double spending is similar to counterfeiting in physical currency, but the principle is slightly different. Double spending refers to the same digital currency being present at two places at once, whilst counterfeiting is the creation of fake money.
For example: Ben makes two Bitcoin transactions. He spends $10 worth of Bitcoin to purchase a pizza and simultaneously purchases a pair of socks using the same $10 of Bitcoin. Ben successfully double spent Bitcoin as he purchased the pizza and the pair of socks with the same funds.
Double spending attacks
There are different avenues where double spending attacks can take place. These include 51% attacks, unconfirmed transaction attacks, and the Nothing at Stake problem.
51% attack
Some attacks occur not because of bugs in the code or security breaches, but simply from playing by the rules. The Proof of Work consensus mechanism consists of a network of miners that agree on the current version of the blockchain. If an entity wants to manipulate the blockchain to double spend coins, they would need to acquire more than 50% of the network’s computing power, hence the name 51% attack.
Although a 51% attack on a Proof of Stake is possible. It is highly unlikely. Attackers will need to obtain more than 50% of the native cryptocurrency’s supply and lock them up in a staking contract. Acquiring 51% can be extremely expensive and in most cases, the circulating supply is not large enough. On top of that, the attacker also risks losing all of their staked cryptocurrency.
Key Takeaway
Smaller networks are more susceptible to 51% attacks. The bigger the network, the more expensive it would be for an attacker to acquire the necessary hardware.
Unconfirmed transaction attacks
Unconfirmed transaction attacks are aimed at unsuspecting merchants who accept transactions that have not been appended on the blockchain. These attacks are very technical that often require precise timing and a very specific sequence of events to occur.
Race Attack
A Race Attack involves unconfirmed transactions. An attacker would create a transaction from their wallet to the merchant and simultaneously create a second transaction from their wallet to another wallet owned by the attacker. The merchant may accept the payment from the first transaction and transfer the goods but won’t receive the cryptocurrency when the fraudulent transaction gets approved first. In the end, the attacker would’ve received the good/service from the merchant whilst keeping their coins.
In the blockchain, the first transaction to be confirmed will take precedence over the other. The attacker would also attach higher fees on the fraudulent transaction to have priority.
Finney Attack
Finney attacks work similarly to a Race Attack, but it requires a miner. The miner would add a transaction from one wallet to another onto a block, but not broadcast the block to the network. A second transaction is made by the miner from their wallet to the merchant’s address. Once the recipient accepts the payment, the miner broadcasts the block with the first transaction which takes precedence over the second.
Did You Know?
Finney attack is named after Hal Finney, who was the first to describe the problem in 2011. He was also the recipient of the first Bitcoin transaction, and many believed Hal to be Satoshi Nakamoto, the alias behind Bitcoin’s creator.
Nothing at Stake
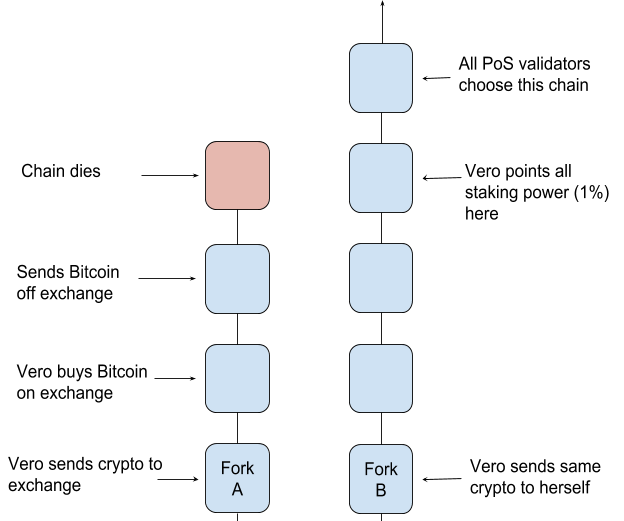
The Nothing at Stake problem is a theoretical security hole that centres around attacking the forks of Proof of Stake blockchains. The problem has not occurred yet in the real world, but it’s an issue that developers are addressing.
When a blockchain forks, it creates a copy that runs in parallel. When one of the chains grows longer than the other, it will become the main chain and the other will become discarded. There is a financial incentive for validators to build on both blocks. Validators risk losing block rewards if the chain they built on gets discarded.
Key Takeaway
The Nothing at Stake problem assumes that every validator will act maliciously and build on both chains. Most validation software only allows the validator to build on a single chain, so the problem assumes every validator will be using modified software.
Such an attack requires both chains to run in parallel until the transaction has been accepted by the merchant. For both chains to run in parallel, it will require every validator to build on both chains. Two transactions are made simultaneously. The attacker will send the cryptocurrency to the merchant on one chain and sends the same cryptocurrency to themselves on the other chain. Once the merchant accepts the payment and transfers the goods, the attacker will focus their staking power on the second chain. Which in turn, will undo the transactions made to the merchant and return the cryptocurrency to the attacker.
How to prevent double spending
Centralized systems
Centralized systems rely on trusted third-party institutions like banks, payment processors, and automated clearing houses to verify transactions and prevent double spending. These systems aren’t as complex as decentralized systems and will have fewer loopholes to abuse. However, this design creates a single point of failure.
Decentralized systems
Decentralized systems use consensus mechanisms to preserve the integrity of the blockchain and protect against double spending. 51% attacks are possible in blockchains, but Bitcoin and Ethereum have never been successfully attacked this way, as the resources required to achieve more than half of the mining power of the entire network will be extremely expensive.
Combating unconfirmed transaction attacks is quite straightforward. The merchant will have to accept the payment once it has been confirmed by the network.
Summary
Double spending allows a user to spend the same digital currency more than once. If this problem is left unchecked, it will undermine the entire electronic asset system. Solving this problem is complex, especially in decentralized systems. Consensus mechanisms makes double spending extremely difficult, but still possible through 51% attacks. Unconfirmed transaction attacks can also be prevented by educating merchants/traders to not accept unconfirmed transactions. At the end of the day, it is extremely important to invest in reputable cryptocurrencies and engage with trusted exchanges.
Disclaimer: The information on Swyftx Learn is for general educational purposes only and should not be taken as investment advice, personal recommendation, or an offer of, or solicitation to, buy or sell any assets. It has been prepared without regard to any particular investment objectives or financial situation and does not purport to cover any legal or regulatory requirements. Customers are encouraged to do their own independent research and seek professional advice. Swyftx makes no representation and assumes no liability as to the accuracy or completeness of the content. Any references to past performance are not, and should not be taken as a reliable indicator of future results. Make sure you understand the risks involved in trading before committing any capital. Never risk more than you are prepared to lose. Consider our Terms of Use and Risk Disclosure Statement for more details.
